If you have been directed to this page, it means that we have detected that your MikroTik router’s DNS server is open to the Internet, and your MikroTik router can be used in a DNS amplification attack.
Our systems automatically disable your Enforcer when this issue is detected, and you are requested to please remedy the issue, before Enabling the Enforcer again.
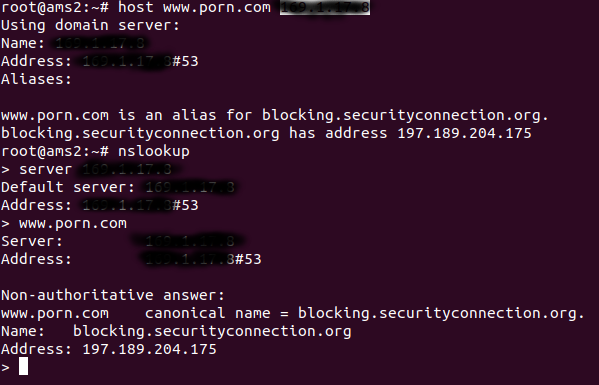
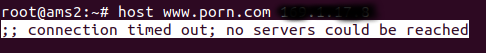
To remedy this issue one simply needs to block the Internet from accessing the MikroTik router’s DNS server service, using the firewall on said MikroTik router.
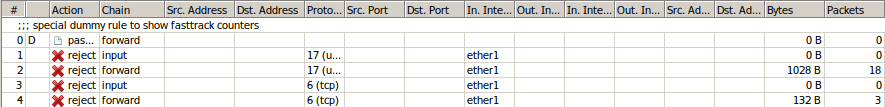
Below, Is an example of a firewall rule that you need to apply to prevent the internet from accessing your MikroTik DNS server.
Via Winbox, if ether1 is your Internet facing port:

Place the above rules above all the other filter rules. Be sure to change ether1 to your Internet facing interface.
We also recommend that you look at the lvcloud DNS intercept under Firewall, NAT, and ensure it only redirects DNS requests from your network, such as LAN interface list, or local network ranges, to the DNS server.
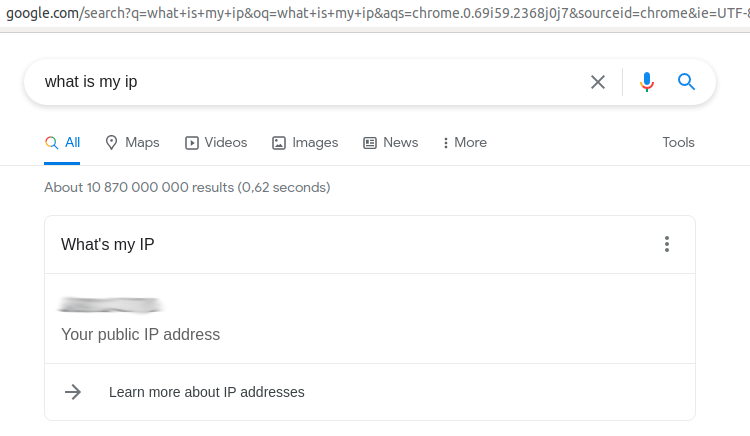
Here is the
Link to check Open Resolver test.
Your Enforcer profile has been disabled in the meantime. Once you have resolved the situation, please feel free to reactivate your Enforcer via the LucidView MikroTik portal. (Scroll down for tutorial).