Security and Intrusion Prevention
LucidView specialises in behaviour-based Intrusion Prevention Systems (IPS) combined with Intrusion Detection Systems (IDS). Our Secure Internet Module is a powerful security tool designed to combat malicious malware and ransomware attacks.
This module continuously monitors all traffic entering and leaving your network, identifying any anomalous activity. Once detected, the suspicious connection is immediately terminated, preventing hackers from gaining unauthorised remote access to your network.
build your enforcer
Activating the IPS on the LucidView App
This video demonstrates how, using the LucidView App and ISP or the customer can quickly protect themselves from intruders.
Behaviour-Based IDS & IPS with LucidView
LucidView specialises in behavior-based intrusion detection and prevention, offering a proactive approach to network security. Our IPS module analyses all traffic connections by assessing their behavior on your network, identifying and eliminating any anomalies in real-time.
Every connection entering or leaving your network is thoroughly analysed and categorised. By examining traffic patterns for any irregularities, the Enforcer swiftly identifies suspicious activity. Any traffic or connection behaving abnormally is immediately flagged as a “Security Risk” and blocked, ensuring your network remains secure.
Activating your IPS using the Portal
This video demonstrates how to activate the IPS feature through the LucidView portal as well as the importance of pulling a security report to ensure that you white list any IP addresses that are important to the running of your network.
Pull and Push Remote Protection
Pull Remote Protection refers to attempts by remote hackers trying to infiltrate your network. The LucidView Enforcer detects these malicious connections and blocks them before they can compromise your network or grant hackers unauthorised control.
Push Remote Protection addresses situations where remote hackers gain access through users within your network, often via VPNs, apps like WhatsApp or Telegram, or even email. In this case, the user inadvertently allows the hacker to push a remote connection into your network. The LucidView Enforcer identifies these push connections and eliminates them swiftly.
The IPS module considers various factors when safeguarding your network against unauthorised access, known malware, and other security threats. While any good IPS solution may occasionally generate false positives—such as flagging VOIP servers or VPNs without DNS entries as security risks—LucidView allows you to whitelist these IP addresses in the MikroTik Portal, ensuring they are excluded from further scrutiny by the IPS module.
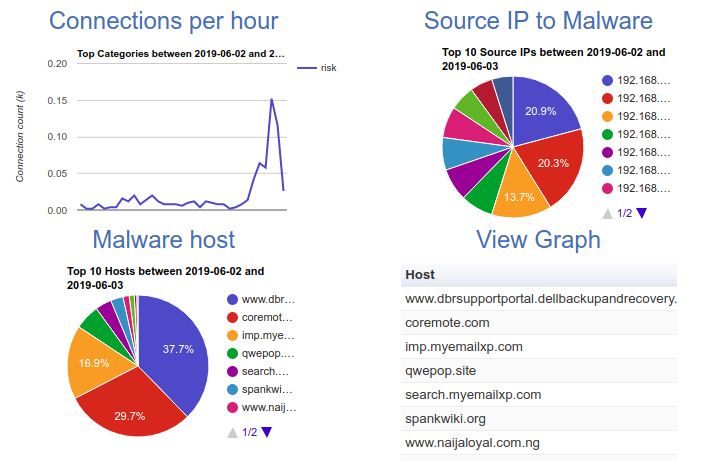
Example of Identifying Security Risks
The charts in this example demonstrate how the LucidView Enforcer thoroughly examines and analyses every connection entering and leaving your network.
Powered by our advanced A.I., the LucidView Enforcer continuously monitors network traffic in real time, instantly detecting any suspicious behavior. When an anomaly is detected, the Enforcer automatically flags the connection and routes it through the IPS module, effectively blocking the threat before it can harm your network.
The LucidView IPS module is designed to swiftly identify and terminate suspicious connections, providing robust Intrusion Detection (IDS) and proactive Intrusion Prevention (IPS) to protect your network from potential security breaches.
How the IPS Security Module works
This is a detailed presentation of LucidView’s behaviour based IPS Security solution presented at the MikroTik Users Conference in February 2020.
