FAQ - How to secure your MikroTik DNS?
How to secure my MikroTik DNS
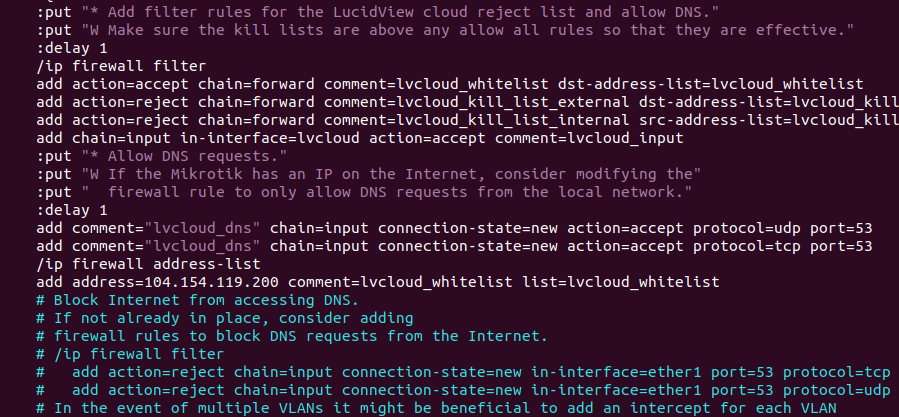
The following are important rules that need to be implemented to block Internet DNS requests:
# Block Internet from accessing DNS.
# If not already in place, consider adding
# firewall rules to block DNS requests from the Internet.
# /ip firewall filter
# add action=reject chain=input connection-state=new in-interface=ether1 port=53 protocol=tcp
# add action=reject chain=input connection-state=new in-interface=ether1 port=53 protocol=udp
# In the event of multiple VLANs it might be beneficial to add an intercept for each VLAN
# The example below shows and intercept for two different VLANs, VLAN1, with gateway 10.31.0.1 on the Mikrotik
# and VLAN2, with gateway 10.31.1.1 on the Mikrotik.
# Please edit and uncomment the example below to suit your environment.
# /ip firewall nat add action=dst-nat chain=dstnat in-interface=VLAN1 protocol=tcp port=53 to-addresses=10.31.0.1
# /ip firewall nat add action=dst-nat chain=dstnat in-interface=VLAN2 protocol=tcp port=53 to-addresses=10.31.1.1
# /ip firewall nat add action=dst-nat chain=dstnat in-interface=VLAN1 protocol=udp port=53 to-addresses=10.31.0.1
# /ip firewall nat add action=dst-nat chain=dstnat in-interface=VLAN2 protocol=udp port=53 to-addresses=10.31.1.1
# /ip firewall filter add chain=input in-interface=VLAN1 protocol=udp port=53 action=accept
# /ip firewall filter add chain=input in-interface=VLAN2 protocol=udp port=53 action=accept
# /ip firewall filter add chain=input in-interface=VLAN1 protocol=tcp port=53 action=accept
# /ip firewall filter add chain=input in-interface=VLAN2 protocol=tcp port=53 action=accept
DNS Escalation Attack
Please also visit the following page on dealing with and preventing a DNS escalation attack.
DNS escalation attack
