FAQ's - Common Causes for MikroTik Enforcer Content Filter Failing
Dynamic DNS Configuration
If an Enforcer has been created and content filtering is not operational, here are some of the likely reasons:
Dynamic DNS entries are entered into DNS settings by the DHCP Client.
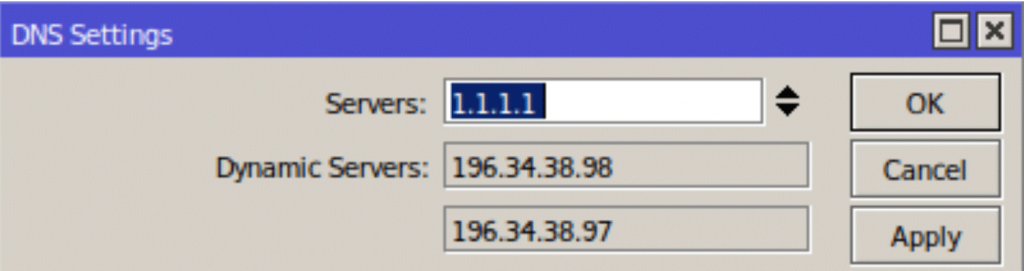
Notice the two dynamic server entries. These are automatically configured by the DHCP client on your MikroTik and override the LucidView DNS Content Filter.
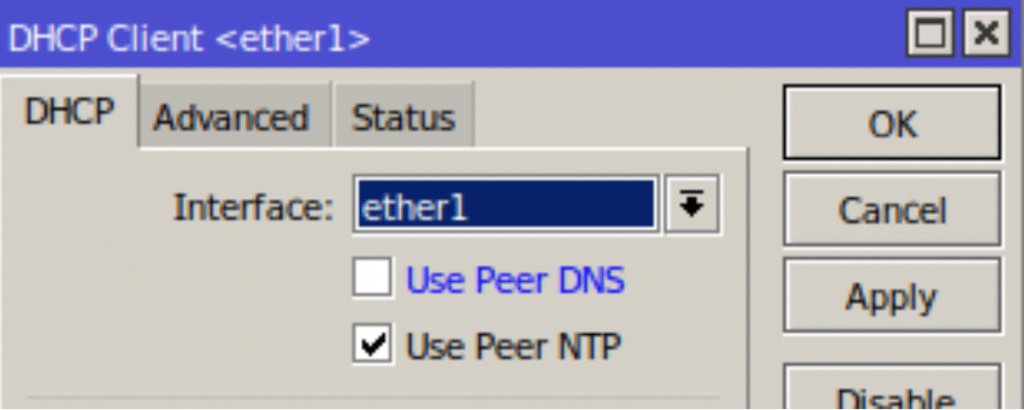
To disable these entries uncheck the Use Peer DNS option under the DHCP client and apply the change. The Dynamic Servers entries should disappear from the DNS settings.
Please also ensure that the DNS intercept is active.
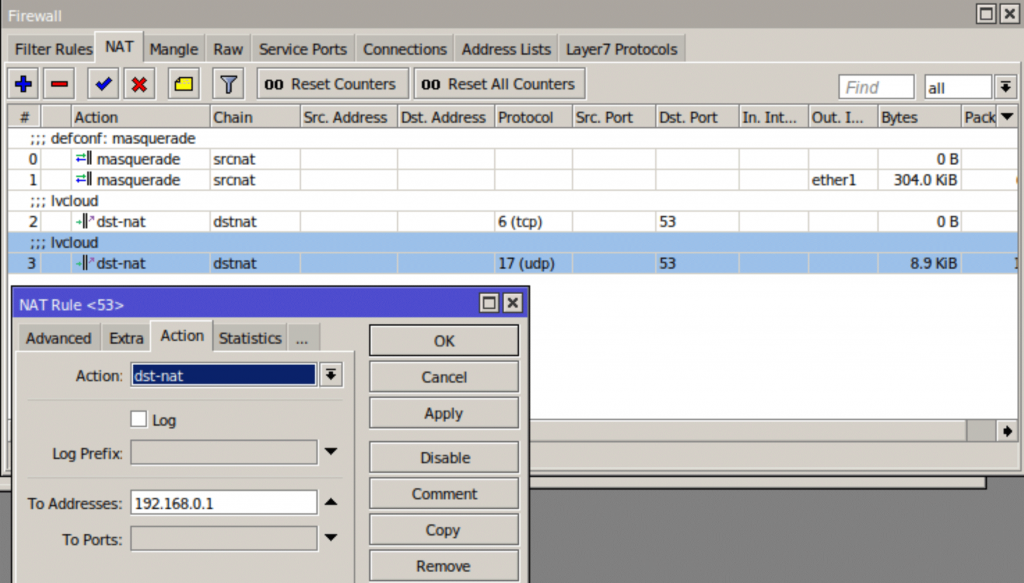
An active DNS intercept will have traffic logged against the Firewall NAT rule.
This makes sure all DNS requests are sent to the DNS server on your Mikrotik so it can be forwarded to the LucidView Cloud.
Please see our Imaging guide video found at https://www.lucidview.net/videos/ and titled “How to build a LucidView Enforcer”, at timestamp 14:30 for common content filter problems.
Firewall block lists.
Two important items to consider for firewall blocking to operate correctly are the Firewall Filter rules, as well as LucidView Cloud access.
Firewall Filter Rules
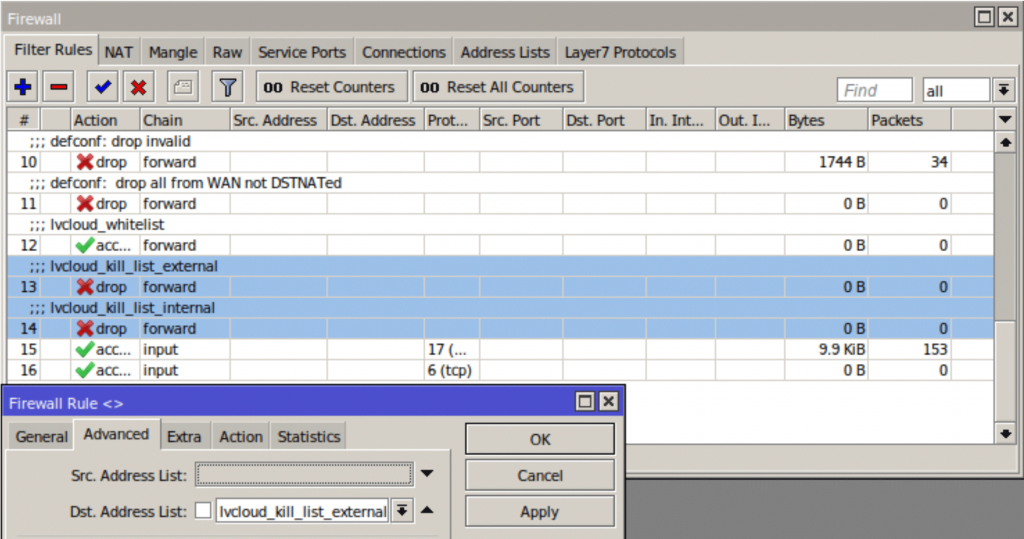
For the Firewall Filter rules, it is important to place the rules above any general allow rules.
LucidView Cloud Access
The LucidView cloud needs to access the MikroTik in order to populate the Firewall address lists, lvcloud_kill_list_external and lvcloud_kill_list_internal.
Please ensure that the user lvcloud has been created and that the ssh key for the LucidView cloud has been added to the lvcloud user. Both the user creation and ssh key are in the bolt on script the portal has created for you.
Back to FAQ's