In last weeks blog, LucidView alerted readers to a strain of malware that is extremely sophisticated and very difficult to isolate and remove. This malware makes use of DGA, or a Domain Generation Algorithm. It has the ability to get through Firewalls as at least one of the numerous domains it has generated is valid and registered, thereby not causing any red flags when passing through the Firewall. Once inside, this malware sets about creating havoc by propagating itself and disabling the built-in protection mechanisms in the operating system.
This week, after much analysis we can say conclusively that what we are seeing is an increase in the Mylobot malware first identified in June 2018. The identification of Malware is the first and most important step necessary to remedy it.
The reasons for a hacker planting this type of malware are always nefarious, at the very least it mimics a DDOS attack, more often than not, it is used to steal data, plant ransomware or maliciously cause embarrassment to the organisation it has infected. The attack comes from inside the network making it extremely difficult to identify and remedy.
This malware is so sophisticated that many of our clients weren’t even convinced they had been infected as their internal Security Operations were unable to detect it, nor was their antivirus software able to see it. Fortunately, LucidView could see the connections being made to the Command and Control server and was able to provide these reports to the security teams to assist them. However, even then, it was extremely difficult for these teams to resolve the Malware, as they had no idea what the malware was. With our analysis this week leading to the identification of this strain of malware which is in fact, a bot, we were able to provide security staff with a diagnosis allowing them to find the best cure for their specific network.
Using our extremely sophisticated Reporting Engine, all traffic in and out of the network is monitored and analysed, this provides us with a lucid and clear view of exactly what is normal traffic and what is anomalous or a deviation from the norm, allowing us to move forward with investigations into exactly what our clients are infected with. Specifically, we were able to see the connections to the Control and Command Centre that the Malware is designed to “phone home” to once it has successfully planted itself within the network, undetected.
After much analysis of the Internet traffic, we knew to be infected, we were able to identify the footprint of the strain of malware that had infected the Networks we were analysing. This Malware has the connection footprint of the very advanced Mylobot. LucidView identified it by matching known domains and IP addresses of Command and Control associated with the Mylobot infection.
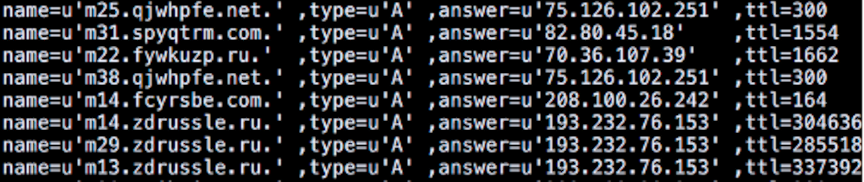
The image above is an excerpt from the analysis on the Centurylink site [1] referenced below. Our Reporting Engine showed a direct correlation between the domains currently reported by LucidView as well as the IP addresses.
The Mylobot Malware is classified as a downloader. This bot, has the ability to execute any executable downloaded from Command and Control which means infected hosts can be used for any nefarious purpose on the local network. At best case, the bot could simply mimic a DDOS attack and cause your business to become unresponsive impacting your ability to provide the services you offer and at worst case, steal critical data for ransom or just sheer malice.
This Malware is extremely dangerous and can be used to steal sensitive data, encrypt it, making it inaccessible to you unless you pay a ransom, and even then there are no guarantees you will be able to access your data.
“Security researchers found a new malware called MyloBot (detected by Trend Micro as TSPY_MYLOBOT.A) that features sophisticated evasion, infection, and propagation techniques” [4]
“The large volume of queries from an individual host can be used as an indication of an infection by this malware.” [1]
LucidView is blocking all known Command and Control connections from infected networks where LucidView is installed, however, as the DNS lookups occur from infected machines this can only be addressed at the workstation level. We can only block the connections that we can identify and with this strain of Malware, we are blocking connections from within the network. However, in the case of BYoD (bring your own device) a device which moves to an unprotected network leaves it vulnerable to both infection, as well as allowing it to communicate with Command and Control. Hence it is imperative that infected devices be quarantined until such time as the Malware can be removed.
“Once installed, the botnet shuts down Windows Defender and Windows Update while blocking additional ports on the Firewall.” [2]
Owing to its sophisticated nature, the malware is difficult to detect and deploys counter measures to protect itself against antivirus and malware software.
Our solution is currently configured to block any known attempts by this and other malware to talk back home, however, this does not negate the risk to your organisation, especially if the particular workstation is a laptop that connects to the Internet via other channels such as 3G or home Internet without LucidView protection.
We recommend urgently taking action to swiftly eliminate the malware from the network.
“It delays 14 days before accessing its command and control servers.” [3]
In other words, if your organisation is seeing this infection now, it is likely you were infected two weeks ago.
Identifying the Malware that is infecting the Network is by far the most important step. A good analogy would be a correct diagnosis of a disease in order to cure it. The ability to see the malware is a key element of the LucidView Reporting Solution.
Now that we have been able to clearly identify what is impacting the network, that is, the Mylobot Malware, security teams can set about finding the best way to remove it. This will differ from one organisation to another depending as their are numerous variables..
With the information provided by the LucidView solution, security teams are now armed with the information necessary to root out the infection.
Please see the references below for more information regarding the Mylobot malware.
[1]https://blog.centurylink.com/mylobot-continues-global-infections/
[3]https://blog.morphisec.com/threat-alert-mylobot-new-sophisticated-botnet

