How Our Internet Management Modules Work
To utilise any or all of the LucidView Enforcer Modules, you’ll first need to transform your MikroTik router into an “Enforcer.” An “Enforcer” is simply a MikroTik router that has run the “Enforcer Profile configuration script.”
This configuration script is generated through the LucidView MikroTik Portal and is specifically designed for MikroTik RouterOS.
To get started, create your account for access to the LucidView MikroTik Portal, where you can create as many “Enforcer Profile configuration scripts” as you need.
If you already have an account, simply log in here.
Activating the Modules for Your Enforcer
By default, the Content Filter and Reporting modules are enabled for every Enforcer profile. To activate additional modules, simply do so via the LucidView MikroTik Portal. For instructions, please refer to our FAQ.
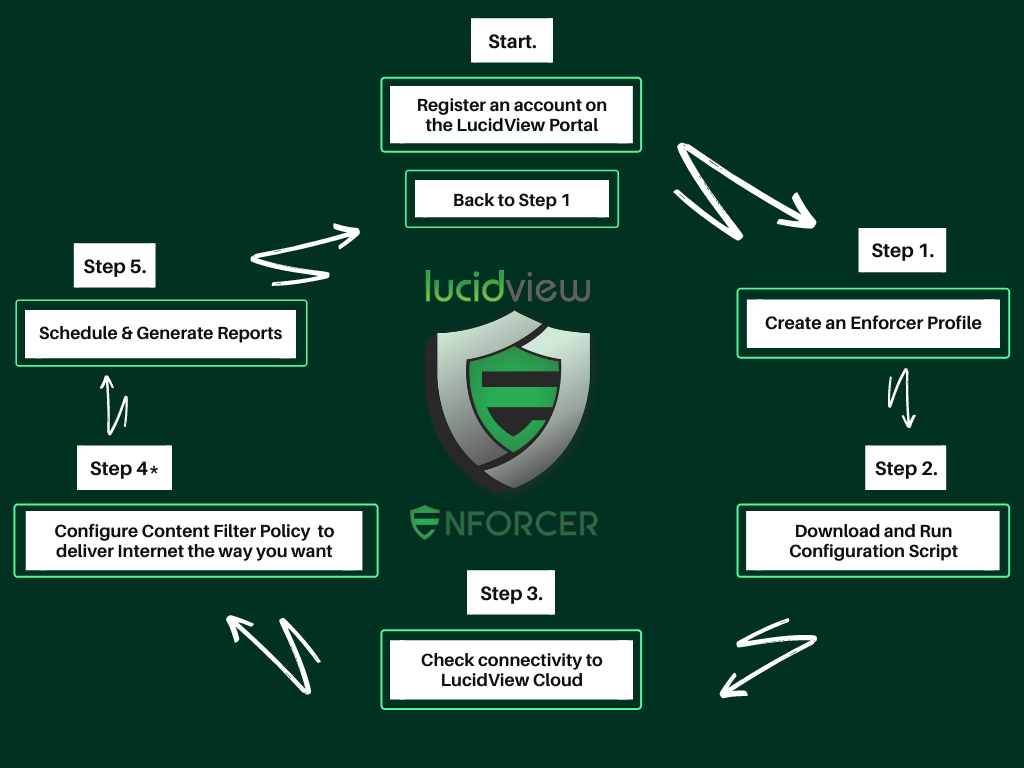
How it Works Overview
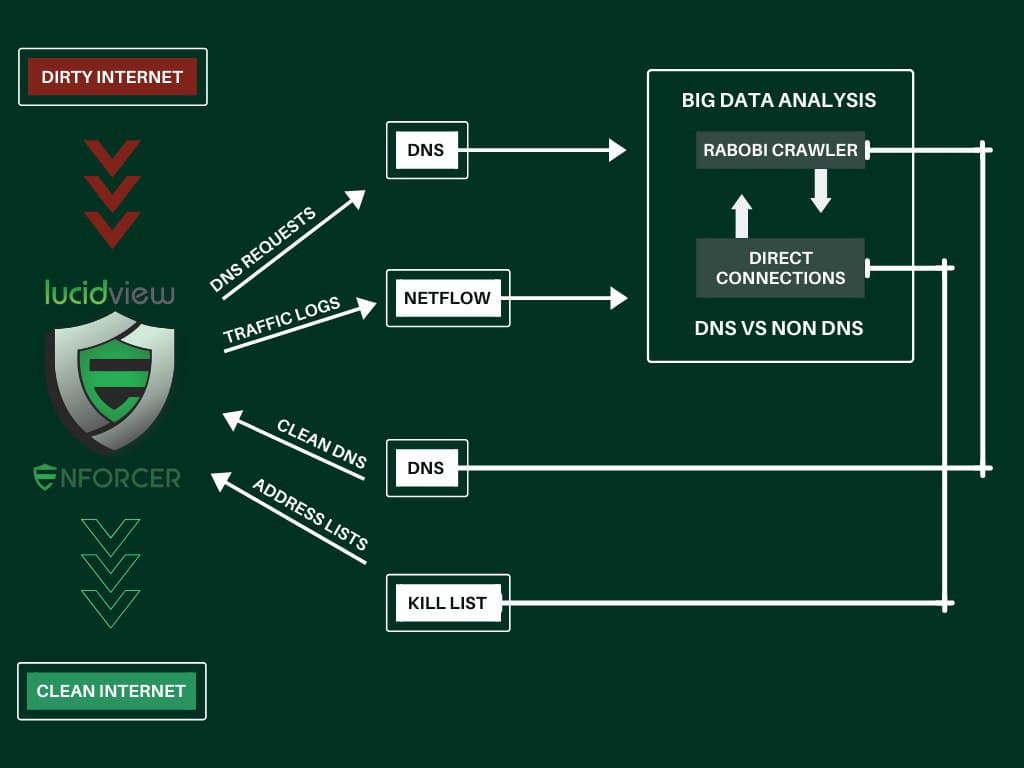
Technically Speaking
Here’s an in-depth technical overview of how the Enforcer works.
After completing your registration, you’ll be able to create your first Enforcer profile. Each profile comes with a configuration script, which needs to be downloaded and applied to your MikroTik router.
LucidView provides a well-commented configuration script for MikroTik routers that essentially does the following:
VPN to LucidView
- Creates a VPN to our cloud.
- Sends Netflow data, which is Metadata ONLY on all the connections going via the MikroTik router. Click here for more information.
- Netflow and Syslog of DNS lookups are sent to the LucidView Cloud via the VPN created.
- Typically Netflow and Syslog will take up less than 1% of the data line, if the line is saturated.
- Configure your MikroTik Router as a DNS server for your Internal LAN and then set up a LucidView DNS server as an upstream forwarder via the VPN.
How Content Filtering Works
Content filtering operates at the DNS level, while Syslog and Netflow data are processed in the cloud. Firewall rules are then sent back to the Enforcer to block any connections that violate the content filter policy, making the Content Filter extremely difficult to bypass.
How Reports, Dashboards, and Traffic-Flow Analysis Work
Syslog and Netflow data are collected in the LucidView cloud, where they are processed and enriched to generate meaningful reports.
This data is then presented in dashboards, providing quick insights into your network traffic-flow. Each dashboard allows for deeper analysis, so you can drill down to identify infected devices, suspicious connections, and much more.
Optional: Allow LucidView Cloud Access to Your MikroTik
For additional functionality (listed below), you can create a user on the MikroTik router to grant LucidView Cloud access:
- DHCP Name Lookup: Useful in the Portal reporting section. (Read-only permissions required)
- Set WiFi Password: Allows modification of the WiFi password. (Read and write permissions needed)
All of the above functionality is clearly commented in the provided configuration script, which can be accessed through the LucidView Enforcer Portal.
For step-by-step instructions, videos, and PDF guides on building an Enforcer from your MikroTik router, click the button below.
